Are you tired of being stuck behind firewalls when trying to access your IoT devices? Well, you’re not alone. Many users face challenges when attempting to use RemoteIoT behind firewalls on Windows systems. But fear not, because we’ve got your back. In this article, we’ll dive deep into how you can effortlessly set up and use RemoteIoT even when a firewall is blocking your way.
Imagine this scenario: you’ve spent hours setting up your IoT devices, only to realize that your company’s firewall or home network security is preventing you from accessing them remotely. It’s frustrating, right? But don’t worry, because with the right approach and a bit of technical know-how, you can bypass these limitations without compromising security.
This guide is designed for tech enthusiasts, hobbyists, and professionals who want to master the art of using RemoteIoT behind firewalls on Windows. Whether you’re managing smart home devices, monitoring industrial equipment, or simply tinkering with IoT gadgets, this article will provide you with actionable insights and step-by-step instructions to get the job done.
Read also:Is Candace Owens A Trump Supporter Unpacking The Truth Behind Her Political Stance
Table of Contents
- Introduction to RemoteIoT Behind Firewall Windows
- Understanding Firewalls and Their Impact
- Setting Up RemoteIoT on Windows
- Configuring Firewall Rules for RemoteIoT
- Using Port Forwarding to Access RemoteIoT
- Securing RemoteIoT Behind Firewall
- Troubleshooting Common Issues
- Advanced Techniques for RemoteIoT
- Best Practices for RemoteIoT Deployment
- Conclusion and Next Steps
Introduction to RemoteIoT Behind Firewall Windows
First things first, let’s break down what RemoteIoT is all about. RemoteIoT refers to the ability to remotely access and control Internet of Things (IoT) devices from anywhere in the world. Whether you’re managing a fleet of smart sensors, controlling a home automation system, or monitoring industrial equipment, RemoteIoT makes it possible to interact with these devices seamlessly.
However, the real challenge arises when you’re trying to use RemoteIoT behind a firewall on a Windows system. Firewalls are designed to protect your network by blocking unauthorized access, but sometimes they can also block legitimate traffic. This is where things get tricky. But don’t worry, because we’ll walk you through everything you need to know to make it work.
By the end of this section, you’ll have a clear understanding of why firewalls are important, how they affect RemoteIoT, and why mastering this skill is essential for modern tech enthusiasts.
Understanding Firewalls and Their Impact
Firewalls are like the bouncers at a club—they decide who gets in and who doesn’t. They play a crucial role in network security by filtering incoming and outgoing traffic based on predefined rules. While firewalls are great for keeping malicious actors out, they can sometimes interfere with legitimate applications, including RemoteIoT.
Types of Firewalls
There are several types of firewalls, each with its own strengths and weaknesses:
- Packet Filtering Firewalls: These firewalls inspect individual packets of data and decide whether to allow them through based on specific criteria.
- Stateful Inspection Firewalls: These firewalls track the state of active connections and use that information to make more informed decisions.
- Application-Level Gateways: Also known as proxy firewalls, these devices act as intermediaries between your network and the outside world.
Understanding the type of firewall you’re dealing with is key to configuring it properly for RemoteIoT.
Read also:Cardi B Ethnicity Unpacking The Roots And Journey Of The Queen Of Hiphop
Setting Up RemoteIoT on Windows
Before we dive into configuring firewalls, let’s first ensure that RemoteIoT is properly set up on your Windows system. Here’s a quick step-by-step guide:
- Download and install the RemoteIoT software from the official website.
- Create an account or log in if you already have one.
- Connect your IoT devices to the RemoteIoT platform.
- Test the connection to ensure everything is working as expected.
Once you’ve completed these steps, you’ll be ready to tackle the firewall configuration.
Configuring Firewall Rules for RemoteIoT
Configuring firewall rules is where the magic happens. You’ll need to create specific rules that allow RemoteIoT traffic to pass through without compromising your network’s security. Here’s how you can do it:
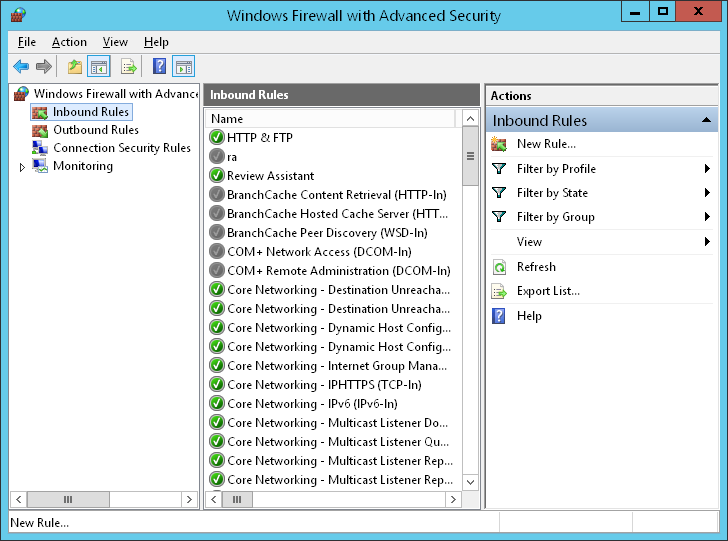
Step 1: Open the Windows Firewall
Go to Control Panel > System and Security > Windows Defender Firewall.
Step 2: Create a New Inbound Rule
Click on "Advanced Settings" and select "Inbound Rules." Then, click "New Rule" and choose "Port" as the rule type.
Step 3: Specify the Port
Enter the port number used by RemoteIoT (usually 8080 or 443) and select "Next."
Step 4: Allow the Connection
Choose "Allow the connection" and proceed to the next step.
Step 5: Apply the Rule
Name your rule (e.g., "RemoteIoT Access") and save it.
Using Port Forwarding to Access RemoteIoT
Port forwarding is another powerful technique that allows you to access RemoteIoT devices behind a firewall. Here’s how you can set it up:
Step-by-Step Guide
- Log in to your router’s admin interface.
- Locate the "Port Forwarding" section.
- Create a new rule and specify the external port, internal port, and IP address of your RemoteIoT device.
- Save the changes and test the connection.
Port forwarding can be a bit tricky, so make sure to consult your router’s manual if you run into any issues.
Securing RemoteIoT Behind Firewall
Security should always be a top priority when working with IoT devices. Here are some tips to keep your RemoteIoT setup secure:
- Use strong, unique passwords for all accounts.
- Enable two-factor authentication whenever possible.
- Regularly update your software and firmware to patch vulnerabilities.
- Monitor your network for suspicious activity.
By following these best practices, you can minimize the risk of unauthorized access and ensure the integrity of your RemoteIoT setup.
Troubleshooting Common Issues
Even with the best-laid plans, things can sometimes go wrong. Here are some common issues you might encounter and how to fix them:
Issue 1: Connection Timeout
Solution: Double-check your firewall rules and ensure that the correct ports are open. Also, verify that your RemoteIoT device is properly configured.
Issue 2: Blocked by ISP
Solution: Contact your Internet Service Provider (ISP) to see if they have any restrictions on specific ports. If so, consider using alternative ports or a virtual private network (VPN).
Issue 3: Security Alerts
Solution: Review your security settings and ensure that all devices are up to date. If necessary, consult with a cybersecurity expert for additional guidance.
Advanced Techniques for RemoteIoT
For those who want to take their RemoteIoT skills to the next level, here are some advanced techniques to consider:
Using SSH Tunnels
SSH tunnels provide an encrypted connection between your local machine and the RemoteIoT device, making it ideal for secure communication.
Implementing Cloud-Based Solutions
Cloud platforms like AWS IoT and Azure IoT offer robust solutions for managing and accessing IoT devices remotely. These platforms often include built-in security features and scalability options.
Exploring Mesh Networking
Mesh networking allows multiple devices to communicate with each other without relying on a central hub. This can be particularly useful in large-scale IoT deployments.
Best Practices for RemoteIoT Deployment
To ensure a successful RemoteIoT deployment, here are some best practices to keep in mind:
- Plan your network architecture carefully to optimize performance and security.
- Document all configurations and settings for future reference.
- Regularly test your setup to identify and address any issues early on.
- Stay informed about the latest trends and technologies in the IoT space.
By following these best practices, you’ll be well on your way to mastering RemoteIoT behind firewalls on Windows.
Conclusion and Next Steps
In conclusion, using RemoteIoT behind firewalls on Windows is entirely possible with the right approach. By understanding firewalls, configuring rules, and implementing advanced techniques, you can unlock the full potential of your IoT devices.
We encourage you to share your experiences and ask questions in the comments section below. Additionally, feel free to explore other articles on our site for more insights into the world of IoT and technology.
Remember, the key to success is persistence and a willingness to learn. So, go ahead and give it a try—you’ve got this!